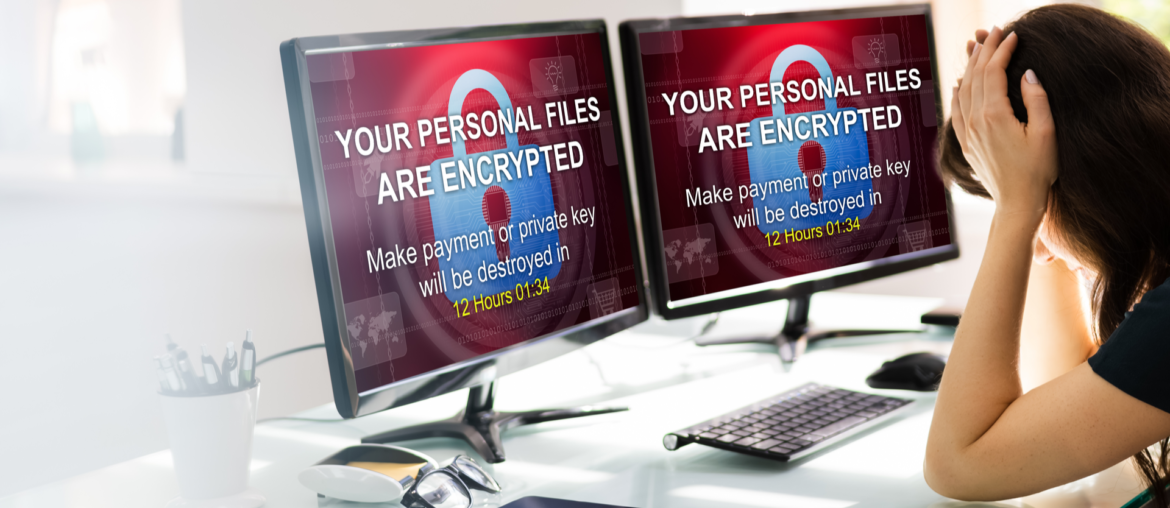
Security news is very clear: ransomware is the new, big threat to business. But what is ransomware?
Ransomware is a specific type of malware. Instead of corrupting your system or searching for particular data, it encrypts files on your network. The attackers then send you a threat to either release the information, or simply prevent you from accessing your devices. Ransomware is a huge security threat, particularly if your data is integral to running your business.
As frightening as these types of attacks are, we can take the threat and turn it into a lesson. Remember: cybersecurity is more than just installing malware removal applications. It is a holistic security protocol that trains your people to recognize a threat and respond appropriately.
So let’s take a deep dive into the world of ransomware, malware, and the kind of cyber attacks that can seriously threaten your business and personal data.
What is Ransomware and How is it Different from Other Malware?
Malware
The best way to think about the difference is that “malware” refers to a wide range of harmful programs that can attack your network or your devices. It encompasses all sorts of malicious software including:
- Trojans – malware that misleads users as to its true intent
- Rootkits – malware that gives somebody total control over your devices
- Adware – malware that causes advertisements to appear on your system when you attempt to access other data
- Spyware – malware that keeps track of your network or system activity and reports back to the attacker
- Worms – malware that is self-replicating, so it can spread rapidly through a network and be difficult to remove
- And so many more
There are absolutely some malware threats that are several of the above, but these categories help security experts better understand how to respond to a specific threat.
Ransomware
Like the malicious software mentioned above, ransomware is a specific kind of malware. Unlike other types of malware, however, the purpose is specifically to hold your data hostage.
A ransomware attack generally looks something like this:
- An employee gets an email that appears to be from IT asking them to download and install a particular piece of software.
- The employee clicks the software link on their business computer and might even go through a setup process on one or more devices.
- The ransomware identifies important data on the device and encrypts them with a unique key.
- The attackers issued a threat that if a certain amount of money isn’t paid, the files will remain locked or, in cases like the CD Projekt hack, released on the Dark Web.
Ransomware attacks grew by 150% in 2020 from previous levels. And all of the evidence suggests that it will continue to rise for quite some time. Security experts are scrambling to respond to this threat, especially since the biggest vulnerability is the human element.

Why Ransomware Attacks Are Suddenly So Popular
It’s not always easy to really pinpoint the reason why ransomware has become the preferred malware of so many hackers, but we can make some educated guesses.
Ransomware Results in Direct Money
Unlike other types of malware, ransomware attacks provide a direct route to immediate cash. Holding business data hostage is a quick way for a lot of hackers to get paid by the victim rather than having to find a buyer for that data elsewhere. While spyware is useful in many ways, for example, anything that the software transmits back to the attacker must then be sold. Negotiations are often with canny buyers who know how much data is worth. They might not get paid for a long time, or at all.
When they use ransomware, however, they are at best dealing with cybersecurity experts who are unlikely to know the cost of data on the black market. Business leaders will be more inclined to pay quickly.
The most surprising thing about ransomware is that it took this long to become so popular. The proliferation of cryptocurrency like Bitcoin and Dogecoin, which allow for entirely anonymous transactions, has helped a lot. Previously, it was a lot more difficult to arrange secure financial transfers. These days, almost anybody can have a cryptocurrency wallet ready to accept ransomware demands.
Ransomware Software is Hard to Remove
The ransomware software is more difficult to deal with since it can literally prevent certain actions. As we mentioned above, malware categories can overlap. Some ransomware is also paired with a rootkit that gives complete control over your system. This would allow the hacker to not only install any software they wanted but also keep the ransomware on there.
Paired with code that makes a worm dangerous, ransomware can self-replicate and install itself all over the network. Ransomware attacks are particularly difficult to detect in advance and can do serious harm to your business before you even have a chance to respond.
Ransomware Works on Lots of Devices
Unlike other types of malware, ransomware is fairly device-agnostic. That means that it can work on a Mac as easily as a Windows machine. It can be easily adapted to mobile devices. That Mac laptop or iPad are as vulnerable to it as your Windows PC or Android phone. Why?
Because ransomware takes a beneficial system and turns it against the device. In this case, we’re talking about “encryption.”
Encryption is a great way for you to protect your files from outside agents. In fact, it’s a key part of how a VPN works.
The way that encryption works are by scrambling your data in a specific way. In its scrambled form, it can’t be accessed. But if you have the right key, it can unscramble the data so that you can use it. This is often used to secure specific files on your computer and, even more commonly, safely send data over the Internet. It’s a crucial part of modern online security and you probably use it without even realizing it.
But, like how an autoimmune disease turns your own immune system against you, encryption can be used to hurt your business with ransomware.
The important words above are “if you have the right key.” In the same way that you can increase your security with a good lock, you can hurt it if you don’t have the key to that lock. High-level encryption protocols are easily available online and often come standard with your Internet-connected devices. Your security software frequently already has the tools involved. This is why, in the same way, that you store sharp knives so they can’t accidentally cut someone, you need to be careful.
Who is Ransomware a Threat to?
There are lots of people who can be the target of ransomware. Unfortunately, it costs the hacker nearly nothing to make these attacks. So it’s possible that individuals might be targeted as well as companies, just for smaller ransoms. That being said, there are a few targets that are particularly attractive to ransomware attacks.
Business Systems
The biggest potential target for ransomware is large companies. The reason is obvious: they tend to have the most money, so they are more likely to consider ransoms of even a few million dollars a write-off. But there’s more to the thinking than that.
We’ve mentioned on this blog (and on social media and even in this very article) that the most vulnerable part of any security system is the people using it. No matter how strong your protection is, one person foolishly downloading a file infected with ransomware can put it all at risk. This is especially true when you have a lot of computers on the same network.
And large businesses employ lots of people, any of whom can be the ransomware’s way into the system.
Plus, ransomware can also be a form of revenge against companies that anger specific people. I mentioned the attacks on CD Projekt above. The release of Cyberpunk 2077 partially motivated these specific attacks. The game shipped with countless bugs and was unplayable on major console systems, which angered a lot of hardcore gamers who were particularly excited to play it. Since there tends to be significant overlap between gamers and black hat hackers, it’s possible that this was seen as vengeance against the business.
Wealthy Individuals
While companies have more vulnerabilities, the wealthy tend to have easier ones to exploit.
Wealthy individuals still have sensitive and important information on private or home systems, but they generally lack the security infrastructure that keeps ransomware off their business network. A home Mac tower can be an even more attractive target simply because it’s unlikely to have robust security software present on a business computer.
What makes this even worse is that a lot of high-powered people will work in their homes or personal devices. Whether it’s writing reports on that Mac mentioned above or reading emails on an unsecured phone, valuable company data could be at risk from ransomware or other types of malware.
Specific people aren’t usually targeted by ransomware for a number of reasons, though. First of all, they have less money to pay and, if they are as vulnerable as they seem, might not know how to use cryptocurrency. Victims are more likely to take personal attacks personally, resulting in a decreased chance of payment and an increased chance of law enforcement getting involved. Most importantly, there’s a higher chance that a specific person just doesn’t have anything they care about losing on their computer.
While these ransomware attacks happen, they are rare. Less targeted malware is much more likely than ransomware.
Medical Organizations
Black hat hackers running ransomware want, more than anything, a quick payday. The longer the transaction, the more likely they will get caught. Many ransomware attacks are targeted at medical organizations.
The sad fact is that this type of ransomware is particularly effective because people’s lives might be on the line. Something as simple as not knowing a patient’s medicine allergies can kill them. So installing ransomware software on a hospital system, for example, can result in very quick payments.
And it’s not just medical groups that are at risk. Law offices frequently have confidential files and important documents they need immediate access to. Government agencies with lax security might pay quickly just to avoid the attack becoming public.
Fortunately, ransomware is not easy to get onto these systems. There are procedural and legal rules in place that make it significantly more difficult to get ransomware on the computer of a doctor than on a fast-food executive. And, of course, if you can’t install the malware software, you can’t do much harm at all.
Ransomware Targets of Opportunity
Not every target is planned out. Sometimes it’s just easy to install ransomware on a system.
For example, a university might make a good ransomware target of opportunity at the start of a semester. New students, many of whom haven’t been briefed on computer security protocols, are more likely to share the wrong file and provide a way into the network. Universities also tend to have smaller budgets for things like IT professionals experienced in dealing with ransomware attacks.
Foil Ransomware With Smart Protection
Because not all malware is the same, it can be difficult to tailor security to meet it. Fortunately, there are a few ways to make your system, while not “immune” to ransomware, certainly ransomware resistant.
Backups Are Kryptonite to Ransomware
The fundamental plot behind getting somebody to install ransomware is to hold their data hostage for money. They don’t want to lose important documents, which could be anything from patient files to family photos. So the most obvious way to foil ransomware is to keep extensive backups.
Being locked out of them is no big deal if you regularly back up your important files. You can erase the entire system and start again fresh, free of ransomware or any malware.
Adding some redundancy is also a good idea when it comes to backups. For example, having a home NAS (Network Attached Storage) lets you not only back up whatever local files you want but keep different versions. So it’s possible to restore your system to a point before you got infected with ransomware. But on top of that, you can keep your most important documents on a reliable cloud server. If the security on your NAS falls entirely apart, you still have access to a malware-free backup. Moreover, professional cloud storage services are generally better defended against ransomware and other malware than your home computer.
Prevent Ransomware Targeting with a VPN
As we mentioned above, encryption can be used for good or for evil. In this case, a VPN can prevent you from being targeted for ransomware.
Ransomware is generally targeted at people that cybercriminals think can pay. But with a solid virtual private network in your corner, it’s harder to tell who you are online. This can make it much less likely that you’ll be targeted at all. Moreover, the use of an encrypted tunnel to send and receive information through a virtual private network will make it even harder to find ways to try and trick you into downloading the ransomware, to begin with.
Improve Your Personal Security Hygiene
Learn how to recognize suspicious online behavior that might lead to you installing ransomware.
Check the email address of anybody sending you a security update at your work address. Is it the person who normally sends things? Is your company’s address spelled right? Has it been signed at the bottom and do they have any additions to their signature that you’re familiar with? If the answer is “no,” then the attached file might be ransomware.
Make sure that the website you’re going to is the one you want. Hackers can use a “Man in the Middle” attack where they hijack your connection and send you to one of their websites instead. Malware can be installed as soon as you get there, or they could be tricking you into downloading ransomware. Look at the URL in the address bar to make sure you’re on the right site and have your anti-virus always updated with the latest ransomware definitions.
Use different passwords for different sites. Don’t share passwords over unencrypted channels. And if you think you’ve been infected with ransomware (or any malware), contact your IT department immediately.
Just because ransomware and malware are serious security threats doesn’t mean that you have to be a victim. In fact, it doesn’t take a lot of effort to protect your system from ransomware. The biggest trick is to be alert. Understand what ransomware can do and, like with any other malware, take appropriate precautions. Not only can this help keep ransomware off your system, but it can also make any successful ransomware attacks moot.
Download PrivadoVPN
Protect your privacy with a world-class VPN. Sign up for premium access to PrivadoVPN and get unlimited monthly data, access to 300+ servers from around the world, and up to 10 simultaneous connections. Get a top-rated VPN that can secure your privacy at home, at work, or on the go.
Sign up for PrivadoVPN today!